(personal) Lessons from Brazil's
Pioneering Experience with e-VotePedro A D Rezende *
Speech at the 07 Votobit Conference
Monterrey, Mexico, September 2007
----
Transcription edited by Pedro A D Rezende

1
Good morning.
I`d like to thank the organizers of Votobit for the invitation and the oportunity to be here today.
I`d like to talk about some personal lessons learned from Brazil`s pioneering experience with electronic voting.

2
The first thing to notice is that it is not only about voting machines.
Brazil`s experience started in 1982, with the electronic tallying of the state election for governor in Rio de Janeiro. The election was on paper ballots, the tallying of precincts was done manually, filled in ballot reports, and these precinct reports were then digitized, for the official election tallying, done by software in a data processing center.
After that, the experience went on to the process of building a national database of registered voters, in 1985. Voter registration and voting in Brazil is compulsory for people between the ages of 18 and 65.
Then it went on to the process of choosing the first models for voting machines and the first procurements, in 1994.
And finally, in 2000, we reached nationwide coverage with an electronic voting system for official elections, under the control of a federal electoral authority.
3
The experience of 1982 has taught us some lessons. This is a picture of an on-line advertisement for a book written by two journalists about that episode. This is possibly the first case of electronic election fraud that we are aware of.
The first lesson we learned from this is that when most undervotes and overvotes (null votes) end up being counted as votes for one particular candidate, this anomaly can either be attributed to a programming error or to a deliberate manipulation.
The second lesson is that if the contracts for software development, deployment and operation for the tallying are done in a certain way, then, when the result of the election is contested in the courts, one can rest assured that there will be no way to identify who is responsible for the error or for the deliberate manipulation.
This is what happened in the first election held for governors in Brazil after twenty years of rightwing military dictatorship, when a leftist candidate in Rio de Janeiro rescue his electoral victory by means of a grassroots effort in manual recount and massive protests, helped by poor performance by the Proconsult software.

4
From Re-registration in 1985, we learned that because storage was at the time expensive, then perhaps the need for precinct officials to be able to visually identify a registered voter was not so important, and, in the process, the picture was taken out of the voter identification document.
This is supposed to be a modernization effort. At least the paper in which the document gets printed by the computer is of a better quality. The lesson here is still incomplete, and perhaps we need to wait for a future edition of Votobit to learn how a lack of picture to identify voters can help someone in the electoral process.
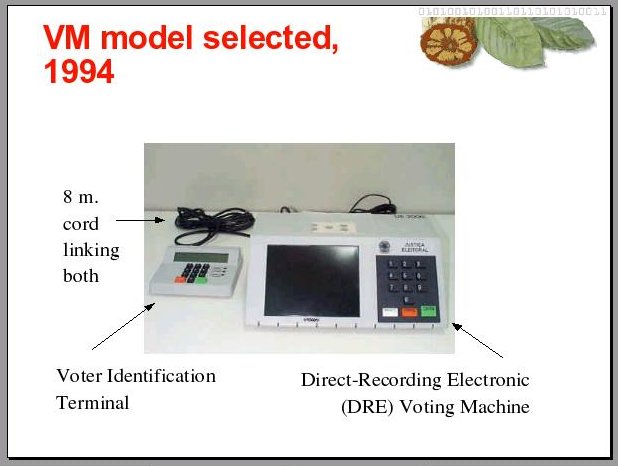
5
Then, in 1994, after several years testing prototypes by several vendors, the federal electoral authority in Brazil decided for this particular model of voting machine. A direct-recording electronic voting machine, which means no physical representation of individual votes is kept in it, only the totals cast are kept in a table in an electronic file.
At the end of the voting this table is printed in a ballot report, as we call it, which is then recorded in an electronic file, encrypted and saved in a diskette to be transported to a data processing center for the final tallying, done by software.
This machine also keeps a list of registered voters that are allowed to vote in that precinct. In Brazil, a voter can only vote in a predetermined precinct, assigned to him at time of registration.
To check that a voter is dully registered to vote in that precinct, to which that particular machine was assigned, the voter identification number is keyed into the terminal, which is linked to the voting machine. So, in short, the identification of the voter, and the votes he casts, are kept in the same machine, in supposedly different files.

6
How do we know that the sequence of voter identities, and the votes they cast, is not matched in a third, separate, secret file? Well, the assurance that we have, that this cord connecting the terminal to the voting machine does not allow this to happen, is the word of the electoral authority.
Of course they say that there is a thorough, verifiable chain of custody, a chain which political party representatives and voters can follow through, to make sure this doesn`t happen, that no such association is kept in any file, but the problem with this thorough, verifiable chain of custody is the following.

7
The last link in this thorough, verifiable chain of custody happens to be a self-validation process. Software from the voting machine is run, to verify if the files found in that voting machine are the ones supposed to be there. And the list of the files supposed to be there is kept in one of these files, named in the script shown here.
Of course they do all sorts of hashes and digital signatures from different, electoral authorities and party representatives and etc., but the detail here is that everything is running in the same platform, at the same time. The verifier is run under the control of the verified, which is very disturbing for a sane security expert, to say the least.
In voting machines used in Brazil in the 2000 election, for instance, in order to disable the self-validation and have the self-validation program return OK regardless of what is found in the machine, all it takes is to comment out two command lines in the configuration file called setup.bat.
This is the same file that controls the start up process in the DOS operating system. In fact, two thirds of the voting machines in Brazil run on an operating system very similar to DOS; the other third run on Windows CE, which is not very different with respect to the control architecture.
Anyway, to disable this self-validation in the last link of this thorough, verifiable chain of custody, all it took in 2000 was to comment out two command lines in a plaintext setup file. With any text editor.
The reason we can say this is because of the only time so far that an independent, expert witness was allowed to look inside a real voting machine. The only time an expert not working under stringent nondisclosure obligations for the Brazilian electoral authorities was allowed to do a post-mortem analysis of a voting machine, for one of the parties in a court case over a disputed election result.
In this case, the expert witness wanted to know if what he found there was supposed to be there. He got no answer from the authorities in two and a half years, so he decided to comment on what he found and published his findings in the case proceedings, in Santo Estevão, Bahia, in 2004, together with the corresponding files. This file is one of them.
In all other cases where election results were contested, no independent expert witness was ever allowed to look inside a preserved working voting machine. They can look at some source code, but only within the headquarters of the federal electoral authorities, for five days only, sixty days before elections, with no access to search or compile tools, and under stringent nondisclosure obligations.
So, thanks to that one and only exception, we now know of vulnerabilities in the self-validation process, which electoral authorities are now quick to discard as already fixed. Since the system’s architecture has not changed, perhaps they are now encapsulating the setup scripts in some binary encoding. If this is the fix, then to disable the self-validation now would require some compiler and source, instead of a simple text editor.
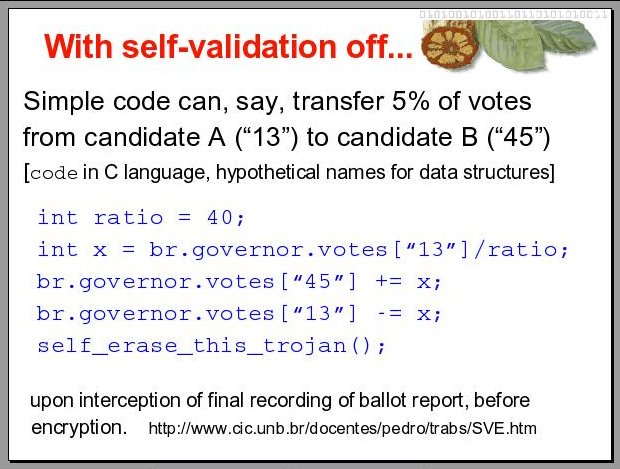
8
With self-validation off, some things can go unnoticed, and not only in the way of mocking vote secrecy. Things like these first four lines of code, for instance, which can transfer a percentage of votes from one candidate to another, on all machines infected with them. And of course, a simple routine can be written to erase these lines and itself, after they run. To have this effect they can be put to run just before the final recording of the ballot report, as it has to be printed in plaintext, which is one step before encryption, to be saved in the diskette for transport to the final tallying.

9
With this model, we learned a lesson about how people get confused with the concept of security. In the technical sense, security is the control of protection mechanisms. And “to protect” is neither an intransitive nor a transitive verb. It is a bi-transitive verb. This means, one protects someone (with some interest) against something (some risk), and not “the system”, especially when the system fields more than two interests. More than two interests at play entail risks of a type known in law as collusion.
Every time I talk about electronic voting, no matter in what language, I run into difficulties at this point, for most people do not know, or care to know, what collusion means. If you have difficulty understanding what I have to say from now on, you still have a chance to save the time you are investing in this talk by later looking up this word in the dictionary.
When the risk of collusion is present, that is, when more than two interests are played out by a system, security becomes a balancing act between risks and duties among the interested parties, which means, a balance between secrecy and transparency. More secrecy is not necessarily good for the parties involved. It is certainly good for the one responsible for running the system, because nobody can figure out if what is going on within the system is what is supposed to happen or not. But not for the overall balance between risks and responsibilities of the parties involved.
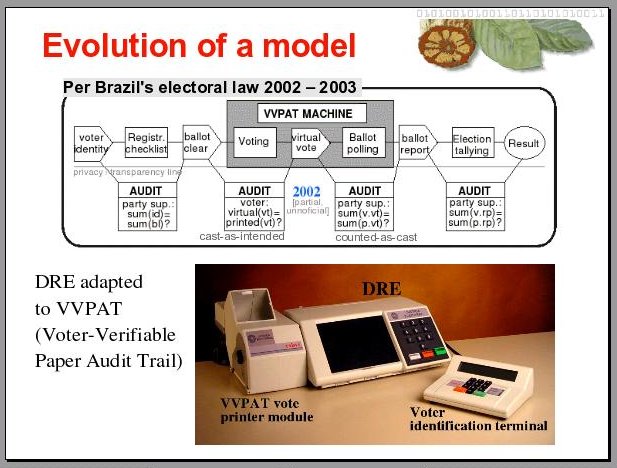
10
Because of some political upheaval that happened in Brazil in 2001, regarding electronic fraud in the Senate’s voting system, the public opinion was mobilized to the point that the law for general elections was changed, mandating that the DRE machines be adapted so as to be able to print a paper audit trail of individual votes, so that the system can allow for recounts if necessary.
The idea is to have electronic ballot reports validated, when needed, by a manual recount of the corresponding individual votes, kept in a plastic bag attached to the sealed printer. Through a glass window in the printer, a voter is able to see, but not allowed to touch, a printed version of the vote he is casting electronically. Upon confirmation, his vote is cut from the paper reel and ejected into the bag by the printer.
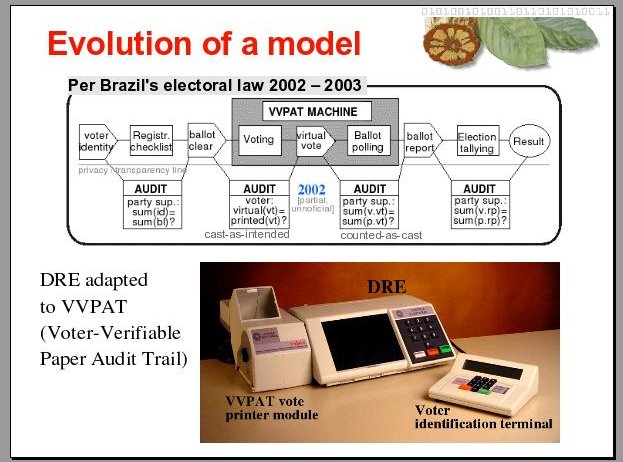
11
But this audit measure never went into effect. The law was changed again in 2003, before the next election in 2004. Before that, electoral authorities managed to negotiate an interim period for this measure to be "tested", during the 2002 elections. Since they were in charge of planning and running the "tests" for the audit measure that could reveal faulty conduct on their part, they were keen to make sure that the test was a total failure.
Of course they blamed the law mandating this type of paper audit trail for recount purposes, as the culprit for all the problems that happened during the 2002 elections. One can understand their posture, for when one tries to introduce a paper audit trail in this manner, in a purely electronic voting system, most of the risks and vulnerabilities we know conventional elections by paper ballot have, are let back into the system.
The lesson here is that, if in one hand this measure can put in check the excess of power given to those who run purely electronic elections, the power of being able to manipulate the process without being deterred, on the other hand it brings back most of the bad things paper ballots are known to have. So perhaps this is not the best solution.
But what we have today in Brazil is probably not good as well, because we’re back at the DRE model in which a vote cast can not be verified by the voter. A voter can not know if the vote that he cast is being counted the way he cast it. And party representatives can not know if the electronic ballot reports that came out of voting machines are not being manipulated in the total tallying, after decrypted and read to the tallying database, when their power is abused.
Precinct officials and electoral authorities are increasingly doing so, defying the law, boycotting the rule that says that each party whose representative asks for a printed version of a ballot report shall have one, at the moment of the closing of the vote, when the electronic report is recorded in the diskette, signed on the back by the precinct official. They are printing copies only for the electoral authorities, for bookkeeping purposes. This is worrisome because if this happens and votes get shuffled during the final round of tallying, after decrypted electronic reports are inserted into the election authorithy central database, there is no way to beat or collect proof of an eventual fraud.
So, what we have here is a system whose security relies entirely in an alleged thorough, verifiable chain of custody where “thorough” and “verifiable” are defined by electoral authorities who happen to be those who design the system, those who write the rules on how it can be supervised or verified, and who judge the result of themselves running the system. In a way that when the result of an election is contested in the courts, they can uphold the means of proof, disqualify the questioning, and brag about the system being so good that its results have never been seriously challenged.
Well, even if the power to decide how this thorough, verifiable chain of custody is to be seriously implemented, even if this power is aimed at balancing risks and duties among all interests involved, there is an intrinsic problem with DREs that is often overlooked. >>12

12
The problem is a principle that is very similar to Gödel’s incompleteness theorem in Logic, and very similar to the Heisenberg’s uncertainty principle in Quantum Mechanics.
It was determined in a PhD thesis in Computer Science, by Doctor Rebecca Mercury at the University of Pennsylvania, defended in 2000, and this principle says, roughly, that a purely electronic voting system can not offer simultaneously the guarantees of vote secrecy and tallying integrity.

13
The Mercury Indetermination Principle in fact sets no hope for a system’s “Thorough, verifiable chain of custody” if “Thorough” is understood to be some balance between risks among potentially conflicting interests involved in the election.
The thing with elections is that they always present more than two potentially conflicting interests: Those of al least two opposing candidacies, who supposedly want to win, those of the electoral officials, who are supposed to run the system for a clean election, and those of voters who want a clean election.
Due to human nature we have to consider at least three of these four players to be holding potentially conflicting interests. And we must not forget that organized crime tend to learn quite well how to use deployed technologies. The work of Dr. Mercury was based on Level 4 assessment of ISO standard for security in information systems known as the “Common Criteria”. It is a very important and decisive theoretical result about elections.

14
The main lesson I learned from following Brazil’s saga, where federal electoral authorities got to hold too much power, in the sense that they write the rules on how a purely electronic system can be audited, supervised or validated, in the sense that they design, procure, contract private parties to develop, set up and operate it on their behalf, while being a branch of the Judiciary that judge their own acts, their own rules, etc., from my experience on following how this works I reached an empirical conclusion, which is my main contribution to the debate on DRE.
This empirical conclusion is that the Indetermination Principle revealed by Dr. Mercury make two conflicting senses of security (with respect to purely electronic voting systems) inseparable and mutually cancelable. And in order to facilitate here I will put my translation that is in the article I wrote for this conference, so you can follow.

15
No wonder when electoral authorities are given too much power, usually at the pretext of having to manage technology, and happen to align with DRE vendors, who like the fact that their clients concentrate power, and in some sense share it with them, over how modern elections can or should be run, no wonder how it is so difficult to have a dialog between those who are interested in preserving the values of democracy, and are worried about the sense of security of voters holding these values, and those who take for granted the DRE model, and think of security for their own sake.

16
The way this dystopia is handled can be well seen by this advertisement, run in a nationwide weekly magazine in Brazil in 1987. This is an advertisement for an IT company called Microtec, and it features Saint Peter pointing to a computer and saying: “without it, life would be hell”. This is a myth that we live today, that most people who are not very versed in technology come to believe, with the help of corporate media, that technology is a solution, or bring solutions for human problems, by their own goodness.
The way this doctrine approaches the problems we are discussing here, about the value of DRE model vis a vis the values of democracy in electronic voting systems, is through a dogmatic approach.

17
It is to turn the indertemination principle discovered by Dr. Mercury into a fable, and to turn the belief in a “thorough, verifiable chain of custody” for DRE-based systems into a act of faith.
The believers of this doctrine are usually people who don’t bother to figure out how an electronic election can be supervised or verified by voters. They don’t care, they think that it is up to people who understand the technology to figure out. And supervise. .
On the other hand, among the ones who understand the technology, those whose also value democracy, they are not been idle. They’ve been observing the scene, they’ve been working on ways to improve voting systems in the direction of balancing risks and responsibilities of the interests involved, where the balance among more than two interests can be preserved, taking into account the indetermination principle that besieges purely electronic systems.

18
Perhaps the best hope in that direction is what is called the End-to-end cryptographic independent verification, a mechanism that can be built into electronic election systems to allow voters to take a piece of the ballot home, a piece that functions as a receipt, but not in the sense of a normal receipt, because it is a receipt that does not allow them to prove to others who they voted for. This will bar them from selling their vote, or from being coerced to show it. But it does allow them to verify that their vote has been cast as intended, and also allow them to, with high degree of accuracy, make sure that their vote was counted properly, or counted-as-cast.
Two examples of working systems that are now in prototype phases are the Punchscan system, by Chaum, and the ThreeBallot system, by Rivest. Ron Rivest is one of the inventors of the digital signature scheme, and Chaum is one the most prolific cryptographers alive, in fact both are. Chaum has several patents under his name, including that of digital cash.
However, as one who follows the points of view I laid down here might expect, these new and promising advances in electronic voting systems does not attract much interest, or sympathy, from election authorities already entrenched with too much power, like the ones in Brazil. Hope still rests with those that were not too early or too easily seduced by the dogmas of the Saint Byte.

The following are some references for this presentation. I thank you for your attention.
Author and Author's rights
* Pedro A D Rezende
Professor of Computer Science at the University of Brasilia,
Coucil member of Intittuto Brasileiro de Política e Direito de Informática.
Presented this keynote speech at the V Votobit, International Coloquium on Electronic Voting, Monterey, Mexico 2007
Copyright
By Pedro A D Rezende
This work published under the license at http://creativecommons.org/licenses/by-sa/2.0/ca/